What is a denial-of-service attack and why do they happen?
A denial-of-service (DoS) attack is a cyberattack in which the attacker tries to disturb the data systems of the target, so that they are unable to work properly. The goal of the attack is to prevent the target from functioning. DoS attacks typically last several minutes, but in some cases the attack can last much longer.
“DoS attacks can be roughly divided into three different types: volumetric attacks, protocol attacks and application layer attacks.”
The goal of a DoS attack is to flood the server with too many requests
In a volumetric (i.e. volume-based) DoS attack, the numbers matter. A volumetric DoS attack takes place when the attacker commands a botnet under their control to attack the target. A botnet is an army of hijacked devices, such as poorly protected IoT devices infected by malware. The target could be, for example, the proxy servers that are vital for a company’s webstore. The goal of a DoS attack is to flood the server with so many requests that it is no longer able to process them all.
In a successful DoS attack, the target service or website no longer functions, or it operates significantly slower. A suitable analogy is a two-lane highway that suddenly receives in one go the same amount of traffic as a ten-lane highway. Because of the sudden traffic congestion, the vehicles are unable to get to their destination as quickly as usual. The same kind of thing happens on the internet – if a packet cannot reach its destination or the server cannot process its response, the service becomes inaccessible.
The majority of DoS attacks these days are “distributed” attacks. This means that the attack is perpetrated by many devices – sometimes dozens or hundreds, but most often thousands or even hundreds of thousands. Attackers try to create a botnet to use in a DoS attack by infecting or hacking into vulnerable devices that are suitable for this kind of attack, such as IoT devices. They can then command those devices to send the target network traffic that is tailored for the attack.
“An increasingly common trend is for DoS attacks to be sold as a service, which has also somewhat lowered the bar for engaging in a DoS attack. Anybody can order a targeted DoS attack online for as little as a few dozen dollars.”
There can be many motives for a denial-of-service attack. Often the reasons are related to politics, activism (“hacktivism”) or harassment for a variety of reasons. It is also becoming increasingly common for criminals to threaten a DoS attack in order to extort money.
How can organisations protect themselves against DoS attacks?
There are a variety of different methods and technologies for preventing DoS attacks. The most appropriate method is a layered defence where several systems are involved in blocking attacks, such as specialised systems for blocking volumetric DoS attacks, firewalls and load balancers. Application servers can also utilise technologies for combatting attacks.
The most common methods of protecting against volumetric DoS attacks is to reroute traffic to pass through a “packet washer”, which can separate malicious traffic from the honest traffic so that services remain available. When this kind of protection succeeds, regular users do not even notice that a DoS attack has taken place at all.
DoS attacks from Elisa’s perspective
During the last year, there have been tens of thousands of high-end DoS attack alerts in Elisa’s data networks, almost all of which were blocked automatically at the network level. This is equivalent to several dozen high-end DoS attacks every day.
The average volume of DoS attacks has been steadily growing throughout the past year. At the beginning of the COVID-19 pandemic as well, there was a clear growth spike in the volume of attacks. In the chart below, you can see clear linear growth in 2020 in the average number of attacks.
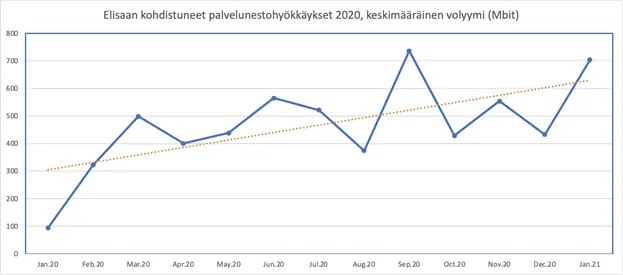
Towards the end of 2020, we also encountered at Elisa another trend that is becoming more widespread, where attackers try to use DoS attacks to extort a ransom.
A large denial-of-service attack has a volume of around 10–100 gigabits. Attacks of over a terabit have also been seen, targeted at large, international institutions and technology giants.
What can consumers do about this?
The botnets used in DoS attacks can comprise masses of devices intended for consumers. A botnet can consist of individual devices as varied as an internet-connected fridge, PC, phone, security camera or other electronic devices.
“If a device does not receive regular security updates, it will very likely become vulnerable to an attacker, ending up as part of one of the many botnets used in DoS attacks.”
Consumers can do a lot to protect their devices. It’s necessary to immediately apply security updates and change any default passwords to strong new passwords.
Read more:






